Well…it looks like the Mac is finally getting hit with malware! I’ve had to remove the “Elf Toolbar” or “Translation Toolbar” aka “Conduit” from a number of Macs in the past few weeks. Judging by the increasing number of recent forum posts on Apple’s Discussion Boards, it’s spreading fast. Here’s what it is and more importantly how to remove it.
Background
I was able to track down some of the actual package installer files for Elf and installed it on a machine with a fresh install of Mac OS X 10.6.6. My testing was performed on that machine. If you’d like a copy for your own more thorough evaluation, please get in touch with me. For obvious reasons, I will not be posting it here.
What is Elf?
Elf appears simply to be adware with several software components. Upon running the installer, I was immediately bombarded with the following.
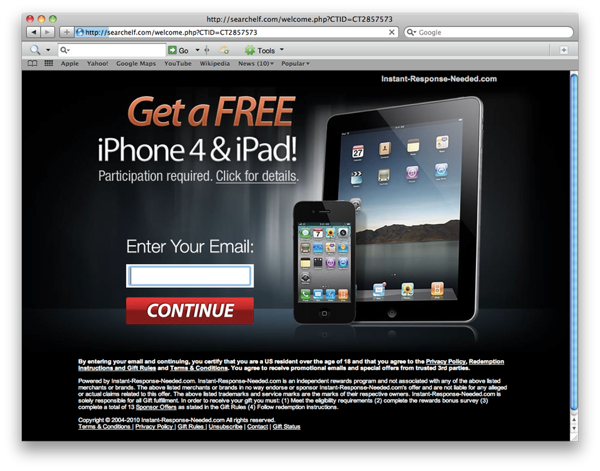
Users of the machines that I removed Elf from reported more frequent advertisements popping up, or even not being able to use the web browser at all. I didn’t experience this, but I only used my infected test machine for a few hours. Notice the toolbar right below the
address bar. This is installed with Elf, somewhat “hacked” into Safari window. In fact, if Safari was open before you installed Elf, you’d now see two copies of Safari in your Dock.
Some other lovely things that come with Elf are an “alert” menubar icon. This icon seemed to only be present when Safari was open.
To go along with these alerts is an awful (oh, I mean “handy“) alert dialog, complete with close button on the wrong side of the window.
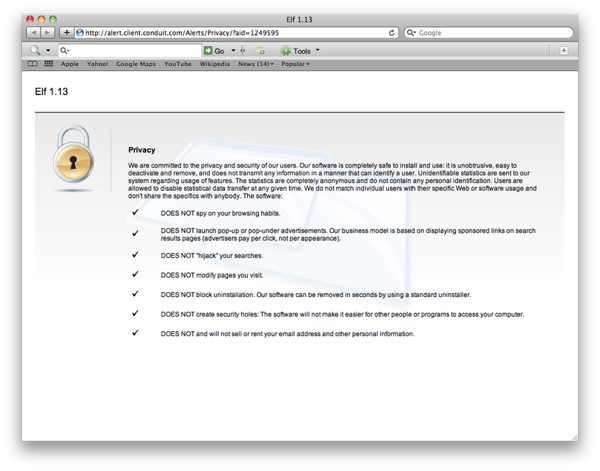
Clicking the icon dropped down a list of choices which displayed websites like the following “Privacy Policy” (not sure I believe it):
I also thought that Elf might be messing around with iCal due to the iCal icon looking very strange after installation and the fact that the Elf toolbar includes a calendar component. I couldn’t find any evidence to back it up, but I’m not sure what else would cause what’s pictured below. You’ll see below that the iCal icon’s font is different. After launching iCal, the font was fixed, but the strange font would come back on reboot.
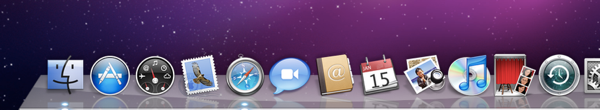
How did I get it?
No one I’ve talked to seems to know how it got installed on their system. Judging from the .pkg files, it looks like they were downloaded via drive-by. The only problem with this is that Elf installs files to areas of your Mac that require administrative access. This means at some point _you authorized the installation_ with an administrator username and password!
Update: A commenter suggested people have downloaded this by clicking a fake download link while trying to download Mac software. This might be a picture of such a fake download link.

What does it do?
I used the utility fseventer from fernLightning as well as the contents of the .pkg files I acquired to track file system usage after the installation. The files I noticed touched by Elf are listed in the “uninstall instructions” section below. The toolbar portion is actually a product (a “Community Toolbar (ct)”) from Conduit. I’d imagine the different toolbars could have different portions of malcode, but the uninstall steps should be the same since they’re based off the same product.
Some scripting additions and a system LaunchAgent are installed in addition to the pieces you’ve seen above. The toolbar itself is actually an InputManager (“one of the simplest and most popular ways to load arbitrary external code into other applications” — cocoadev.com). There are good InputManagers (most notably those from Unsanity), but they routinely cause instability with the OS in my experience.
Other than install a bunch of garbage and occasionally pop up ads, Elf didn’t really seem to do too much in my tests. The Conduit LaunchAgent sat in the background, so even if you killed it, launchd would open it right back up (by design). I did notice outbound connections to various flash game, online radio, and ad websites with every new Safari window opened. There was at least one connection per window. Using Wireshark, I was also able to see that Google Analytics code was being downloaded every so often as well. I did not notice any personal information being sent out, though that’s not to say there wasn’t any (again, if you’d like a copy for your own evaluation, let’s get in touch).
How do I get rid of it? (Uninstall Instructions)
Oddly enough, the program does come with a utility called “uninstall.” I didn’t try it out until I had manually uninsalled it though, so I’m not sure what it does. I didn’t feel like doing another fresh install of OS X to find out.
Here’s what I did to uninstall. Run these commands in the Terminal (Applications > Utilities > Terminal). As always, be careful with sudo commands. If you don’t know what you’re doing, ask someone who does. Quit all programs first to be on the safe side.
rm -rf ~/Library/Application Support/Conduit
launchctl unload -w -S Aqua /Library/LaunchAgents/com.conduit.loader.agent.plist
sudo rm -rf /Library/Application Support/Conduit
sudo rm -rf /Library/LaunchAgents/com.conduit.loader.agent.plist
sudo rm -rf /Library/InputManagers/CTLoader
sudo rm -rf /Library/ScriptingAdditions/ct_scripting.osax
sudo rm -rf /Applications/Toolbars
That should do it, you might want to reboot for good measure afterwards, but you shouldn’t have to. Remember to always think before authorizing a program with an administrator username and password. Ask yourself why that particular program needs your password, and don’t provide it if you can’t figure it out. Never run a program that you don’t know where it came from. You might also want to not allow Safari to automatically launch files after download. Remember, no operating system is invulnerable to attack and you are your own best defense.